Emergency IT Support Services
Transform critical incidents from business disasters into manageable disruptions through specialized intervention expertise that amplifies your operational resilience. From system failures to security breaches, we deliver emergency support and recovery services that minimize downtime while establishing prevention frameworks for future stability.
Our emergency IT support expertise bridges the gap between reactive firefighting and proactive system hardening, enabling faster recovery without sacrificing security or compliance standards. Whether you’re facing unexpected system outages, leadership transitions, or cybersecurity incidents, we provide the technical leadership and execution excellence that turns operational emergencies into learning opportunities for enhanced resilience.
Get Your Emergency IT Assessment Schedule Crisis Response ConsultationWhy Emergency IT Support Matters for Your Business
The modern technology landscape has created unprecedented vulnerabilities that extend far beyond simple system downtime. When critical systems fail or key personnel suddenly become unavailable (bus factor scenarios), organizations face cascading business disruptions that traditional IT support models simply cannot address effectively.
The Hidden Costs of Emergency Response Delays
Most businesses drastically underestimate the true cost of inadequate emergency
response capabilities. Beyond immediate revenue loss from system downtime, extended
outages create lasting damage through customer trust erosion, regulatory compliance
violations, and competitive advantage deterioration. When your primary database
crashes, your payment gateway fails, or a key technical leader suddenly departs,
every hour of delayed response compounds the business impact exponentially.
The shift toward cloud-first, distributed architectures has simultaneously increased
system complexity and reduced internal expertise for managing crisis situations.
Cloud-related emergencies often stem from regulatory compliance issues, data
residency violations, or misconfigured global availability settings that create
legal and operational risks extending far beyond technical functionality.
Modern Threats Demand Specialized Response
Cybersecurity incidents, particularly ransomware attacks, have evolved beyond simple
technical problems into complex business continuity challenges requiring immediate
threat containment, systematic recovery procedures, and comprehensive security
hardening. The uncertainty and potential data exposure risks accompanying security
breaches demand expert intervention that addresses not just the immediate attack
vector but the underlying vulnerabilities that enabled the breach.
Without
proper emergency response protocols, these incidents can escalate from minor
configuration problems into regulatory investigations and substantial financial
penalties. Organizations that invest in professional emergency IT support gain
competitive advantages through reduced recovery times, enhanced system reliability,
and improved regulatory compliance.
Quick Wins – Measurable Solutions
Emergency IT support delivers immediate value through specialized intervention capabilities that minimize business disruption while establishing prevention frameworks. Our approach focuses on practical improvements in recovery capabilities, system stability, and operational continuity.
Immediate Crisis Intervention & System Recovery
Deploy specialized technical teams to address critical system failures, security breaches, or infrastructure emergencies. Our emergency response protocols include system stabilization, rapid diagnostics using monitoring tools, and systematic recovery procedures designed to restore business continuity. Emergency interventions include real-time system diagnostics, threat containment procedures, and data recovery operations.
Leadership Transition & Project Takeover Management
When organizations face sudden CTO departures or need to inherit projects from departed team members, we provide transition management that prevents operational disruption. Our approach includes technical audits, digital asset security, and knowledge transfer protocols that preserve institutional expertise while positioning systems for enhanced performance and reliability.
Proactive Monitoring & Prevention Systems
Implement monitoring systems that identify potential issues before they escalate into critical incidents. Our monitoring capabilities include automated alerting, performance tracking, and basic prevention strategies that reduce emergency frequency while improving response effectiveness when incidents occur.
Digital Asset Protection & Security Hardening
Comprehensive protection for domains, payment gateways, intellectual property, and financial systems through access control management and security protocol implementation. Our security approach includes basic vulnerability assessment and configuration improvements that establish defense mechanisms against both technical failures and security threats.
Our Proven Development Approach
Emergency response success isn’t just about rapid intervention—it’s about transforming critical incidents into opportunities for enhanced resilience and operational improvement. Our approach ensures every emergency intervention minimizes immediate business disruption while establishing frameworks for preventing similar incidents and improving system reliability. The essential components of our emergency response approach include:
Proven Methods for Maximum Business Impact
This structured approach has been developed through various critical incident responses, ensuring you benefit from both immediate crisis resolution and practical resilience improvements.
Our Emergency IT Support Development Expertise
Our emergency IT support capabilities span crisis management scenarios from immediate intervention through basic resilience building. Rather than treating emergencies as isolated incidents, we approach crisis response as opportunities to strengthen technology systems through systematic improvement and practical prevention.
Immediate Crisis Intervention & System Recovery
Emergency response teams deploy specialized capabilities with incident response plans, communication protocols, and escalation paths for different crisis types. Our methodology encompasses immediate system stabilization using monitoring tools, diagnostics with threat assessment, and systematic recovery procedures that prioritize business continuity. We maintain emergency access protocols and documentation systems enabling response without compromising security standards.
Specialized Emergency Scenarios & Leadership Transitions
CTO transition management prevents operational disruption through immediate technology assessment, critical digital asset security, and knowledge transfer protocols that preserve institutional expertise. Our project takeover procedures address inheritance challenges from departed team members or external vendors, beginning with infrastructure assessment and documentation analysis. We establish stakeholder communication channels, implement version control protocols, and create knowledge bases ensuring smooth transitions.
Cybersecurity Incident Response & Threat Containment
During cyberattacks and ransomware incidents, we provide immediate threat containment and systematic recovery addressing both attack vectors and underlying vulnerabilities. Our security-focused approach includes audits with vulnerability scanning and configuration management reviews. Security protocols cover access control management, data protection measures, and compliance requirements supported by documentation and incident response procedures.
Cloud Infrastructure Emergency Management & Compliance
Cloud-related emergencies often involve regulatory compliance violations, data residency issues, or misconfigured security settings requiring immediate architecture assessment and remediation. Our cloud emergency services include compliance verification, data residency auditing, access control configuration, and performance optimization helping organizations navigate complex environments while ensuring adherence to regulations.
Monitoring & Basic Prevention Systems
We implement monitoring systems that provide insights into system health, performance metrics, and potential failure indicators through automated alerting and basic analysis. Our monitoring infrastructure covers response times, error rates, system availability, and resource utilization while tracking incident metrics for improvement. Basic prevention systems identify issues through pattern recognition and resource consumption analysis with automated threat detection triggering response protocols.
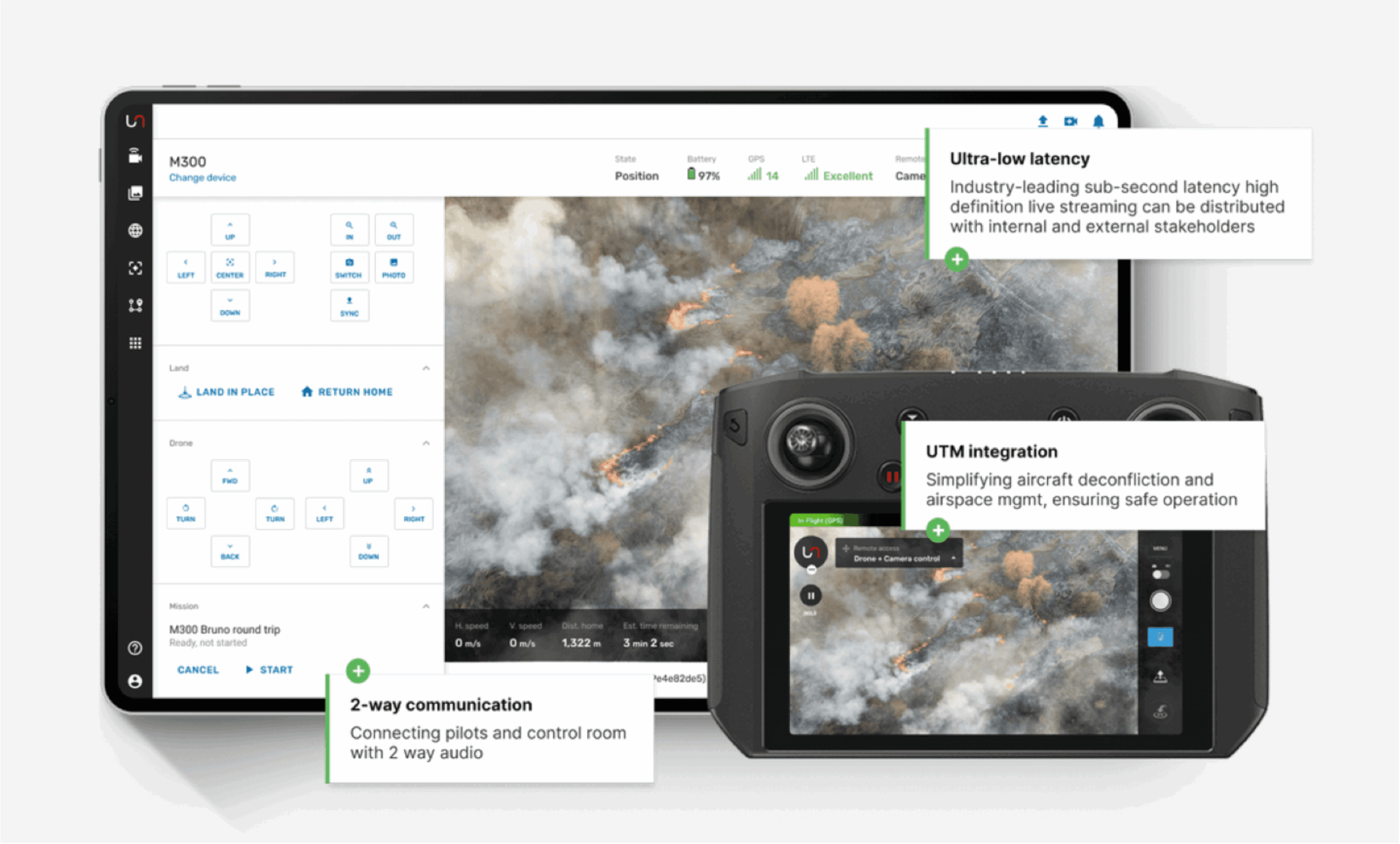
Featured Case Study:
Unleash – Enterprise App Stability Excellence
The Challenge
Unleash, a leading global AI video analytics enterprise solution provider serving
clients across Australia, Europe, and the USA, faced stability and reliability
challenges with their Android application, Unleash Autofly. As a company operating
at the forefront of AI and aviation technology, providing real-time actionable
data through computer vision, Unleash required application infrastructure that
could match their technology standards while supporting their global client
base.
The existing mobile application suffered from performance issues and operational
challenges that threatened the sophisticated AI analytics platform. With clients
depending on real-time data processing, application instability created business
risks and operational inefficiencies that demanded expert intervention.
Our Solution Approach
Understanding that Unleash’s technology leadership position required application
infrastructure matching their AI analytics capabilities, we designed a stability
enhancement strategy focused on systematic reliability improvements. Our approach
emphasized transparent communication and decision-making based on proven
methodologies tailored to Unleash’s operational context and deployment
requirements.
We prioritized engineering solutions over quick patches,
ensuring improvements would support scalability and operational reliability. The
solution strategy included stability assessment, systematic reliability
engineering, and implementation of basic monitoring designed to prevent future
degradation.
Technical Implementation
Our development team executed application stability improvements through
systematic engineering approaches focused on reliability, performance
optimization, and operational resilience. We implemented monitoring capabilities,
error detection systems, and performance optimization measures ensuring consistent
application behavior across deployment environments.
The technical execution included systematic code review and optimization,
implementation of testing frameworks, and establishment of monitoring systems
providing visibility into application performance. We established development
practices ensuring ongoing stability maintenance and provided documentation
enabling Unleash’s internal teams to maintain enhanced standards.
Measurable Results Achieved
The impact of our stability enhancement work demonstrates the value of systematic intervention for enterprise technology platforms:
- Significant improvement in networked device interaction enabling better communication and coordination across distributed systems
- Enhanced application functionality for smaller businesses while maintaining scalability for larger enterprise deployments
- Improved application stability and reliability addressing previous performance issues and operational inconsistencies
- Better user experience across deployment environments ensuring more reliable functionality regardless of operational conditions
”The Unleash team recognized the value of our systematic approach to stability enhancement, particularly our focus on sustainable solutions rather than temporary fixes. Our commitment to transparent communication and collaborative problem-solving aligned with their values for technical excellence and operational reliability.”
Key Lessons and Strategic Applications
This partnership reinforced important principles for emergency response and stability enhancement: systematic engineering approaches deliver more sustainable improvements than quick fixes, basic monitoring and documentation help prevent future stability degradation, and collaborative technical partnerships enable faster resolution of operational challenges. These insights continue to inform our approach to emergency response and system stability enhancement across different technology platforms and business contexts.
Spectrum of Services – Zero to Hero
Emergency IT support success depends on matching response capabilities to crisis severity and organizational requirements. Our service spectrum approach ensures you receive appropriate intervention for current emergencies while establishing foundations for enhanced preparedness capabilities.

Basic Emergency Response (Reactive Intervention)
Immediate crisis intervention focusing on system restoration and issue resolution through emergency diagnostics, system recovery procedures, and threat containment. This reactive approach prioritizes business continuity and minimal downtime through established response protocols and recovery methodologies. Emergency response includes basic documentation and immediate stabilization without comprehensive prevention framework implementation.
Proactive Monitoring & Response (Enhanced Preparedness)
Implementation of monitoring systems with response protocols designed to identify and address issues before they escalate into critical incidents. This level includes automated alerting mechanisms, performance tracking systems, and preventive maintenance procedures that reduce emergency frequency while improving response effectiveness. Monitoring implementation provides early warning capabilities and systematic response coordination.
Comprehensive Incident Management (Complete Response)
End-to-end incident management including root cause analysis, systematic problem elimination, and prevention strategy implementation. Services extend beyond symptom treatment to address underlying vulnerabilities and implement solutions preventing similar incidents. This level includes documentation systems, basic compliance frameworks, and knowledge transfer ensuring organizational resilience improvement.
Predictive AI-Powered Prevention (Advanced Intelligence)
Advanced failure prevention using AI-powered diagnostics, automated recovery systems, and intelligent threat detection. This highest tier includes predictive analytics identifying potential issues before symptoms appear, automated response procedures handling routine interventions, and continuous optimization of emergency prevention capabilities through analysis of system patterns and threat indicators.
This progression ensures your emergency response investment scales appropriately with business growth and risk tolerance while maintaining operational excellence and strategic resilience improvement at every level.
Flexible Engagement That Fits Your Business Reality
Emergency situations demand flexible response models that accommodate varying crisis severities, organizational constraints, and business continuity requirements. Rather than forcing rigid engagement approaches, we offer response options that prioritize intervention while maintaining transparency throughout the emergency resolution process. The primary engagement options we offer include:
- Emergency Response Support: Crisis intervention teams for specific incidents
- Project-Specific Emergency Support: Focused intervention for defined system issues
- Hybrid Emergency & Prevention Programs: Combining immediate response with basic resilience building
- Emergency Preparedness Assessment: Crisis management framework evaluation
Best for specific incidents requiring technical intervention
Emergency Response Support:
Crisis Intervention
For organizations requiring emergency response capabilities, our support model provides access to specialized crisis intervention teams for specific incidents. You receive technical expertise with communication channels and defined rates for crisis situations. This approach works well for isolated system failures, security incidents, or organizational transitions where emergency response requirements are clearly defined. We maintain emergency contact protocols ensuring response when crisis situations arise.
Ideal for defined system issues with clear scope and resolution requirements
Project-Specific Emergency Support:
Focused Crisis Resolution
When specific incidents require expert intervention, our project-based emergency support delivers crisis resolution within defined scope and timeline parameters. This model works best for isolated system failures, security incidents, or organizational transitions where emergency response requirements are clearly defined and measurable. We provide incident analysis, systematic resolution procedures, and documentation ensuring knowledge transfer while focusing on immediate crisis resolution.
Combines immediate response capabilities with basic resilience building
Hybrid Emergency & Prevention Programs:
Basic Resilience
Some organizations benefit from combining immediate emergency response capabilities with basic resilience building initiatives. This approach provides crisis intervention support while implementing basic monitoring systems, prevention frameworks, and organizational preparedness that reduce future emergency frequency. The hybrid model delivers immediate support through emergency response while building systematic capabilities that enhance operational stability.
Emergency management evaluation and improvement recommendations
Emergency Preparedness Assessment:
Crisis Management Evaluation
For organizations requiring emergency management evaluation, we provide preparedness assessment including emergency response protocol review, prevention system evaluation, and basic monitoring framework assessment. This engagement includes emergency preparedness review, documentation evaluation, and recommendations based on operational requirements and organizational constraints.
Emergency Assessment: Your Starting Point
Every engagement begins with our emergency preparedness assessment process where we evaluate current response capabilities, identify vulnerability areas, and provide recommendations for emergency preparedness improvement. For organizations facing active incidents, this assessment becomes immediate crisis intervention with evaluation of resilience opportunities. This analysis gives you information needed to make informed decisions about emergency response approach and organizational preparedness.
Client Success Story:
Imperative Group
The strongest validation of our approach comes from long-term partnerships where we’ve become integral to our clients’ success. Rather than collecting testimonials from multiple projects, we prefer to showcase the depth and impact of sustained collaboration through detailed case studies that demonstrate measurable business outcomes.
Our Partnership Impact:
- Complete technology leadership for their peer coaching platform serving enterprise clients
- 9+ years of continuous collaboration from startup phase to market leadership
- $7+ million in revenue generation through scalable platform architecture
- Enterprise-grade security implementation including SOC 2 compliance
- Seamless team integration with daily communication and collaborative development
”One of the keys to our success was finding Jacek and Iterators. They’re great communicators. We’ve been in touch almost on a daily basis, collaborating on both a large and small scale. I’ve always had an authentic sense that they’re in it for our success first.”
Key Lessons and Applications
This partnership exemplifies our approach to client relationships—we don’t just deliver projects, we become trusted technology partners invested in long-term success. When clients like Imperative achieve significant business milestones, their success becomes our success, reflecting the depth of partnership that defines our client relationships.
The platform exceeded both customer and QA team expectations, delivering 10% above requirements.
Significant improvement in the interaction among networked devices in the field, empowering businesses while improving app stability and reliability.
Our Technology Expertise
Emergency IT support requires technology choices that prioritize reliable deployment, operational stability, and compatibility with diverse client environments rather than following development trends. We select technologies based on proven performance in operational situations, emergency response capabilities, and alignment with your specific infrastructure requirements.
Backend Technologies for Emergency Response and Recovery
Our emergency response capabilities leverage enterprise-tested technologies designed for reliable deployment and operation under various conditions. Scala and the Akka toolkit provide the foundation for building resilient, high-performance recovery systems that handle emergency workloads efficiently during system restoration operations. Node.js enables deployment of emergency monitoring services and coordination systems, while Python powers our security analysis, automated recovery scripts, and emergency diagnostic capabilities. We also work with Java and Spring Boot for enterprise system integration and compatibility with existing infrastructure.

Infrastructure and DevOps for Crisis Management
Infrastructure and deployment practices ensure emergency interventions perform reliably while maintaining security and compliance standards. Amazon Web Services (AWS) and Microsoft Azure provide the cloud infrastructure foundation for emergency response systems, with containerization using Docker and orchestration through Kubernetes for scalable deployment during various situations. Terraform enables infrastructure-as-code practices ensuring consistent, reproducible emergency response environments. Our deployment processes enable implementation of emergency fixes and recovery systems, reducing manual errors during critical incidents.

Security and Monitoring for Emergency Situations
Emergency response demands security and monitoring capabilities that function reliably while providing visibility into system status and threat indicators. We implement monitoring using DataDog and various specialized security tools for emergency threat detection and system status tracking. Our security protocols include emergency access management, threat containment procedures, and compliance-aware recovery operations. Emergency monitoring systems provide real-time visibility into system health, security status, and recovery progress enabling coordinated response efforts and stakeholder communication.

Data Management and Recovery Systems
Effective emergency response requires data protection and recovery capabilities that function reliably under various conditions. PostgreSQL serves as our primary database for emergency response systems requiring ACID compliance and reliable transaction processing, while specialized backup and recovery tools enable data restoration from various failure scenarios. Our emergency response toolkit includes data recovery utilities, database analysis tools, and specialized recovery procedures for various data scenarios. Emergency data management includes secure backup validation, recovery testing, and compliance-aware data handling.

Why These Technology Choices Matter for Emergency Response
Our technology selections prioritize proven reliability under various conditions and deployment capabilities essential for emergency response, maintainability and vendor support ensuring emergency tools remain available when needed, enterprise-standard security practices and compliance capabilities essential for emergency situations, and operational efficiency that supports sustainable emergency response capabilities. We choose tools that will function reliably during crisis situations and provide clear escalation paths when additional capabilities are needed.

Staying Current While Maintaining Emergency Readiness
Technology evolution continues constantly, and our emergency response capabilities evolve accordingly. We continuously evaluate new emergency response technologies and crisis management approaches, contributing to security research projects and staying engaged with emergency response communities. However, we implement new technologies in emergency response only after testing and validation, ensuring you benefit from innovation without bearing unnecessary risk during crisis situations.

Frequently Asked Questions
Emergency response times depend on situation severity and availability, but we maintain emergency contact capabilities with response typically coordinated as quickly as possible for critical incidents. Our emergency response teams include coordinators who can begin assessment immediately, with technical specialists deployed based on situation requirements and availability. During our emergency preparedness assessment, we establish response protocols including contact procedures, escalation paths, and expected coordination based on your specific infrastructure and emergency scenarios. We prioritize intervention that ensures system stabilization while maintaining documentation for prevention.
Our emergency response includes crisis intervention and system stabilization, incident documentation and analysis, systematic recovery procedures with basic security measures, emergency communications coordination and stakeholder updates, basic prevention framework implementation, and knowledge transfer to your team. We don’t believe in partial emergency support during crisis situations—when we commit to emergency response, we deliver what’s needed for crisis resolution and basic preparedness. Our goal is to provide solutions that restore operations while helping prevent similar incidents.
Security and compliance are built into our emergency response protocols from initial contact through final documentation, not added as afterthoughts during crisis situations. Every emergency intervention follows documented security procedures including access controls, audit logging, and secure communication channels for crisis coordination. We maintain incident documentation for compliance requirements, implement evidence preservation during security incidents, and ensure regulatory compliance throughout emergency response procedures. For clients with specific compliance requirements, we can implement additional security measures including background checks for emergency responders and specialized access controls.
Emergency resolution marks the beginning of our support relationship, not the end of our engagement. We provide post-incident analysis including root cause documentation, implementation of basic monitoring systems to help prevent similar incidents, systematic improvement of affected systems based on lessons learned, and recommendations based on emergency response experience. Our support includes both emergency response capabilities and basic resilience improvements that help prevent future incidents while building organizational preparedness.
Absolutely, and we excel at emergency coordination and collaborative crisis response. We can work as emergency specialists supporting your existing IT team with additional capacity and specialized crisis intervention expertise, take ownership of specific emergency response aspects while maintaining coordination with your team’s ongoing operations, provide emergency coordination while working closely with your technical staff and business stakeholders, or lead emergency response while ensuring knowledge transfer and skill development for your internal team. Our approach is collaborative— we’re here to support your team’s emergency capabilities and institutional knowledge during crisis situations.
Emergency situations vary significantly in scope, severity, and response requirements, and our approach is designed to adapt to different crisis types while maintaining systematic response quality. We handle system failures through diagnostics and systematic recovery procedures, security incidents including ransomware through immediate threat containment and remediation, leadership transitions through immediate asset security and knowledge preservation, cloud infrastructure emergencies through assessment and compliance-aware recovery, and data scenarios through specialized recovery procedures and system improvement. Our goal is to provide effective emergency response that addresses immediate crisis requirements while building basic resilience.
Ready to Secure Your Operations Against Emergencies?
Emergency preparedness doesn’t require lengthy planning processes or formal commitments. We believe the best emergency response relationships begin with understanding your current vulnerabilities and response capabilities, and understanding starts with honest conversation about your operational risks and preparedness requirements.
Our emergency assessment conversations help you understand current vulnerabilities, explore response improvement opportunities, and identify what’s possible within your risk tolerance and operational constraints. These aren’t sales calls—they’re collaborative planning sessions where we share insights from similar emergency situations and help you make informed decisions about emergency preparedness strategy. Whether you’re facing an active emergency, validating response capabilities, or planning enhanced preparedness, we’ll provide honest guidance tailored to your specific operational situation and business context.
During our consultation, we’ll explore your current operational vulnerabilities and emergency response capabilities, discuss response improvement opportunities and prevention strategies, provide insights from similar emergency situations and crisis management experience, outline realistic coordination approaches and engagement options that accommodate your operational requirements, and answer your questions about our emergency response process, team capabilities, and crisis management approach. You’ll leave the conversation with clearer understanding of your emergency preparedness options and next steps, regardless of whether we end up working together on emergency response improvement.
We respond to emergency inquiries within the same business day when possible, with emergency consultations scheduled based on availability and situation urgency. Our team includes emergency response specialists who understand both the technical and business aspects of crisis management and operational continuity requirements.
Schedule directly through our emergency contact system for confirmation, call our emergency response line for consultation availability, or email with specific emergency questions and we’ll respond with crisis management insights and guidance. We accommodate your preferred communication style and schedule, including emergency response coordination for active incidents requiring technical intervention.
Our approach to emergency preparedness relationships focuses on providing value in every interaction, whether that leads to formal emergency response engagement or not. We’ve built our reputation on honest emergency assessments and realistic preparedness recommendations, not high-pressure crisis management sales tactics. Many of our emergency response relationships began with informal preparedness conversations that evolved into crisis management partnerships and resilience improvement over time.
The most common feedback we receive about our emergency response process is appreciation for our direct, knowledgeable approach to crisis management and our willingness to share emergency preparedness insights freely, even before any formal engagement begins. We believe great emergency response partnerships start with transparency, expertise, and mutual respect for business continuity requirements—values that guide every interaction from first emergency contact through collaboration and preparedness improvement.

Jacek Głodek
Founder & Managing Partner
of Iterators




